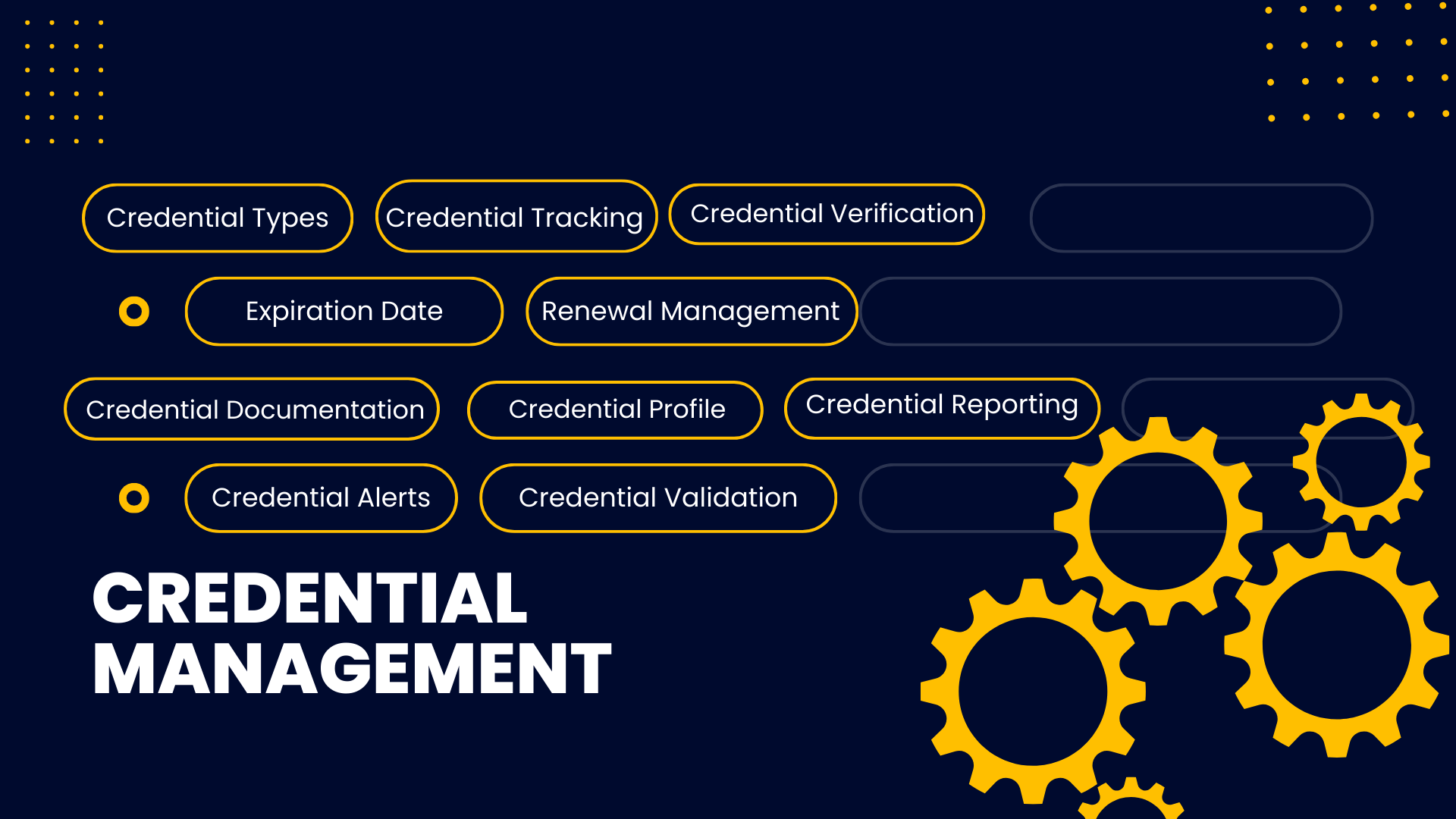
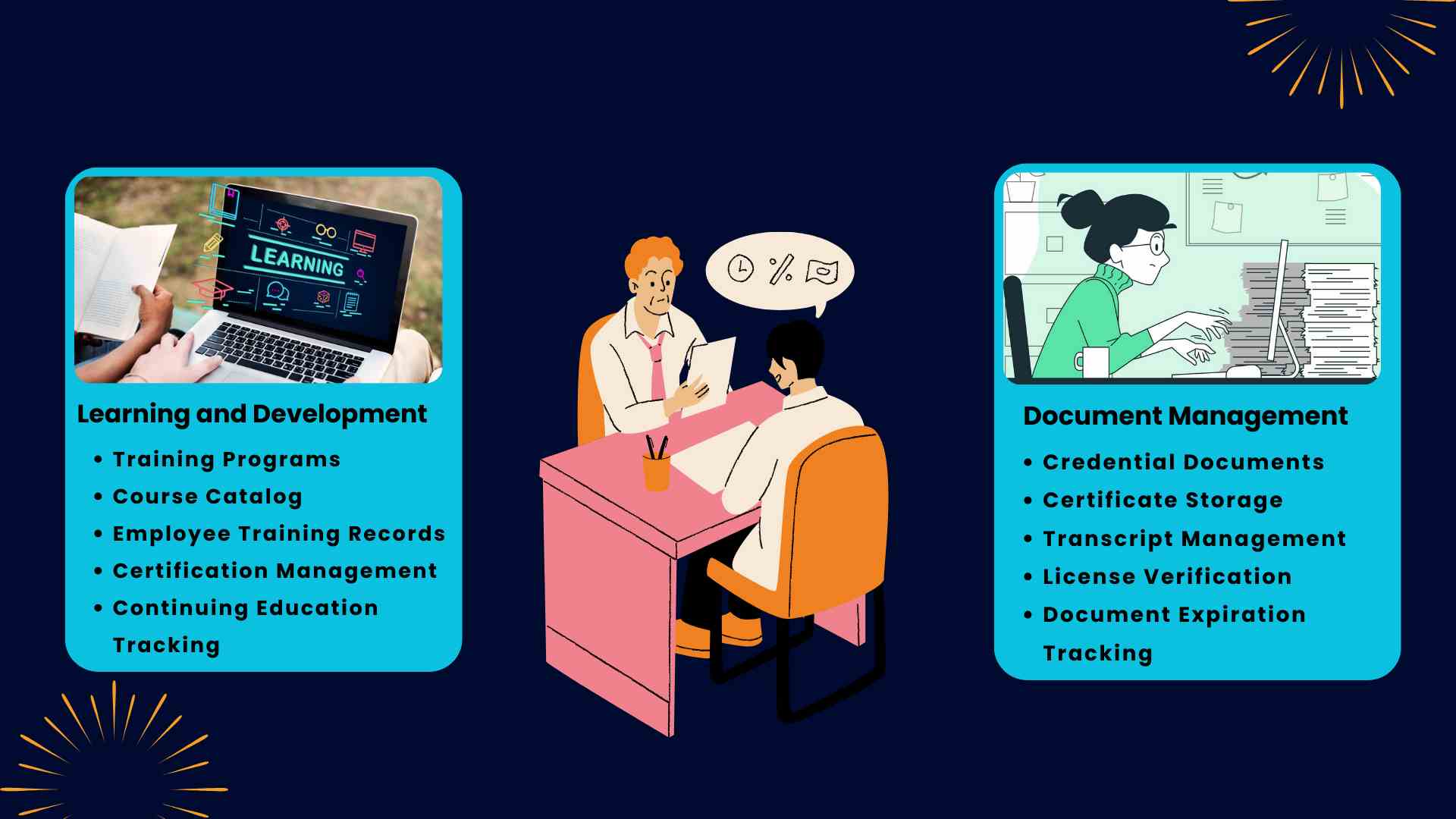
Credential Management
Credential management is the ability to adequately organize and secure credentials responsible for identity authentication and access authorization by monitoring and mitigating vulnerabilities throughout their life cycle. Organizations require user credentials to control access to sensitive data. Deploying a sound credential management system—or several credential management systems—is critical to secure all systems and information. Authorities must be able to create and revoke credentials as customers and employees come and go, change roles, and as business processes and policies evolve. Furthermore, the rise of privacy regulations and other security mandates increases the need for organizations to demonstrate the ability to validate the identity of online consumers and internal privileged users.
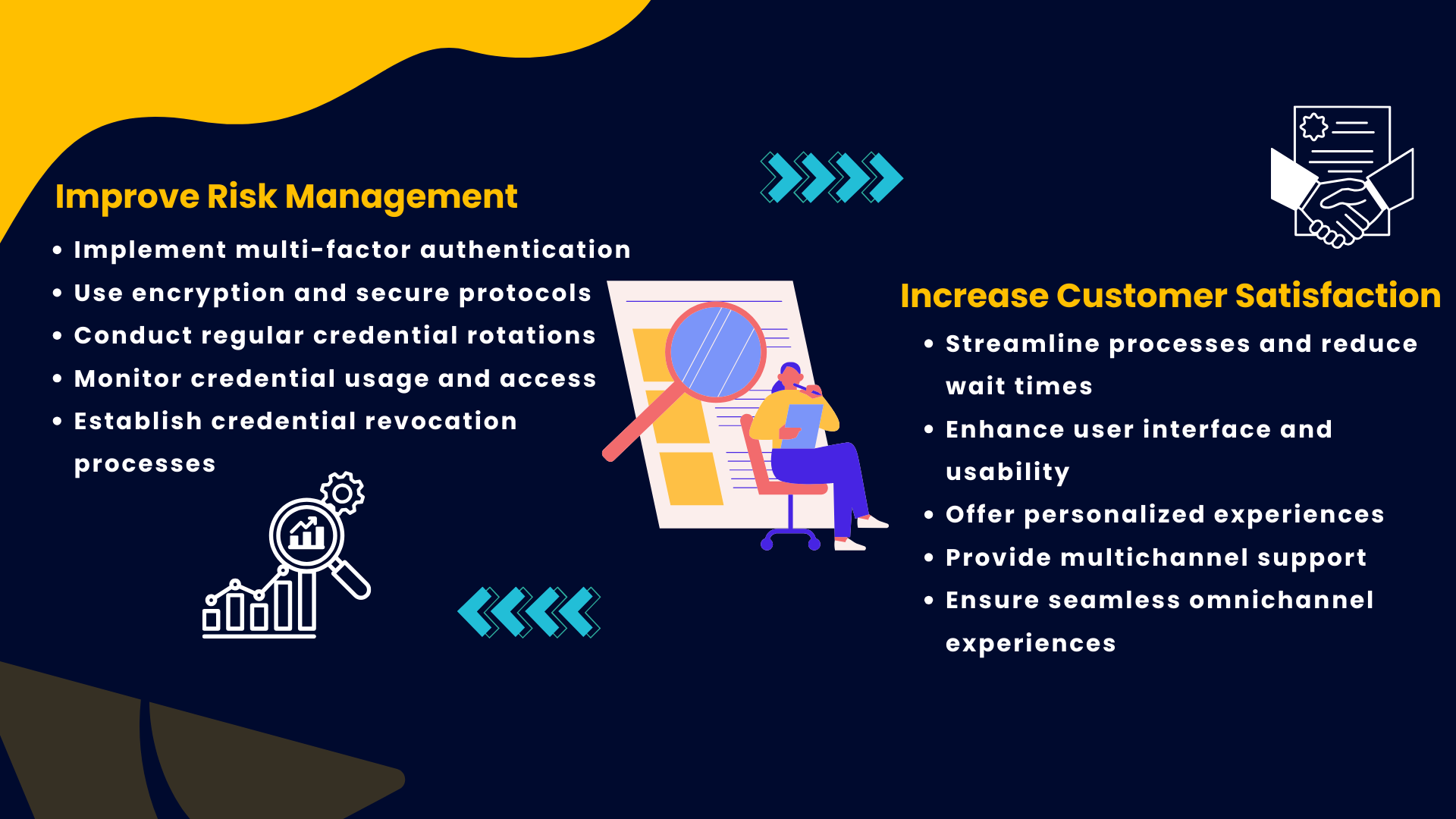
greater efficiency and less waste
Eliminating waste is actually way more important than driving efficiency. Efficiency will help you, but waste will crush you. To waste means to use or expend carelessly, extravagantly, or for no purpose. In business, this usually manifests as time spent on things that don't matter.

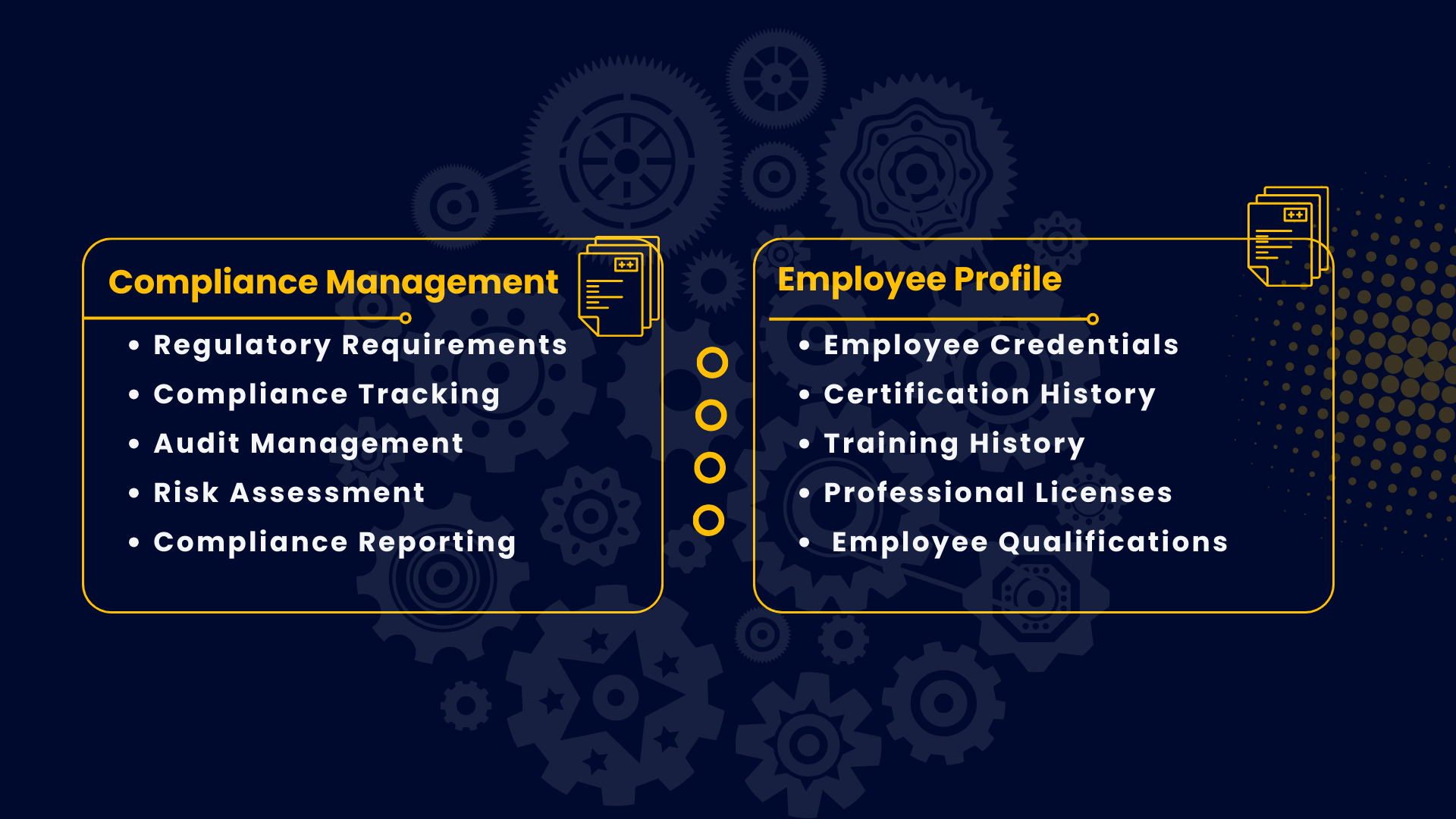
consistent control of major business processes
Process consistency allows businesses to deal with the unknown and react to changes in the competitive landscape. Process consistency allows companies to know when they are doing things right and make changes when they are not.

understanding of customer needs
Customer needs are the psychological and physical motivations that make someone want to purchase a product or service and stay loyal to that business. For example, customers today need quick and convenient ways to reach support online.

managing growth more effectively
Setting goals and aligning growth with those goals will help focus your business's resources effectively and help the business succeed over the long term.

embedded culture of quality
Leaders interested in embedding quality into their organization's culture need to look beyond the use of structures, systems, and processes and pay attention to incentives such as providing employees inspiration (by how the leaders act) and empowerment (so employees feel they have both input and control of their work)

increased profits reduction of costly errors
Negotiating with suppliers, shopping for the best deals, or purchasing bulk. Another way to reduce costs is to cut overhead expenses such as electricity, rent, or salaries. Finally, companies can also increase their profits by increasing sales.

increased customer satisfaction
There's no way of knowing whether your customers are satisfied with your product or what they want you to update or fix, unless you ask them directly and actively listen to their response. Listening and responding to your users helps you retain more customers and build product loyalty.
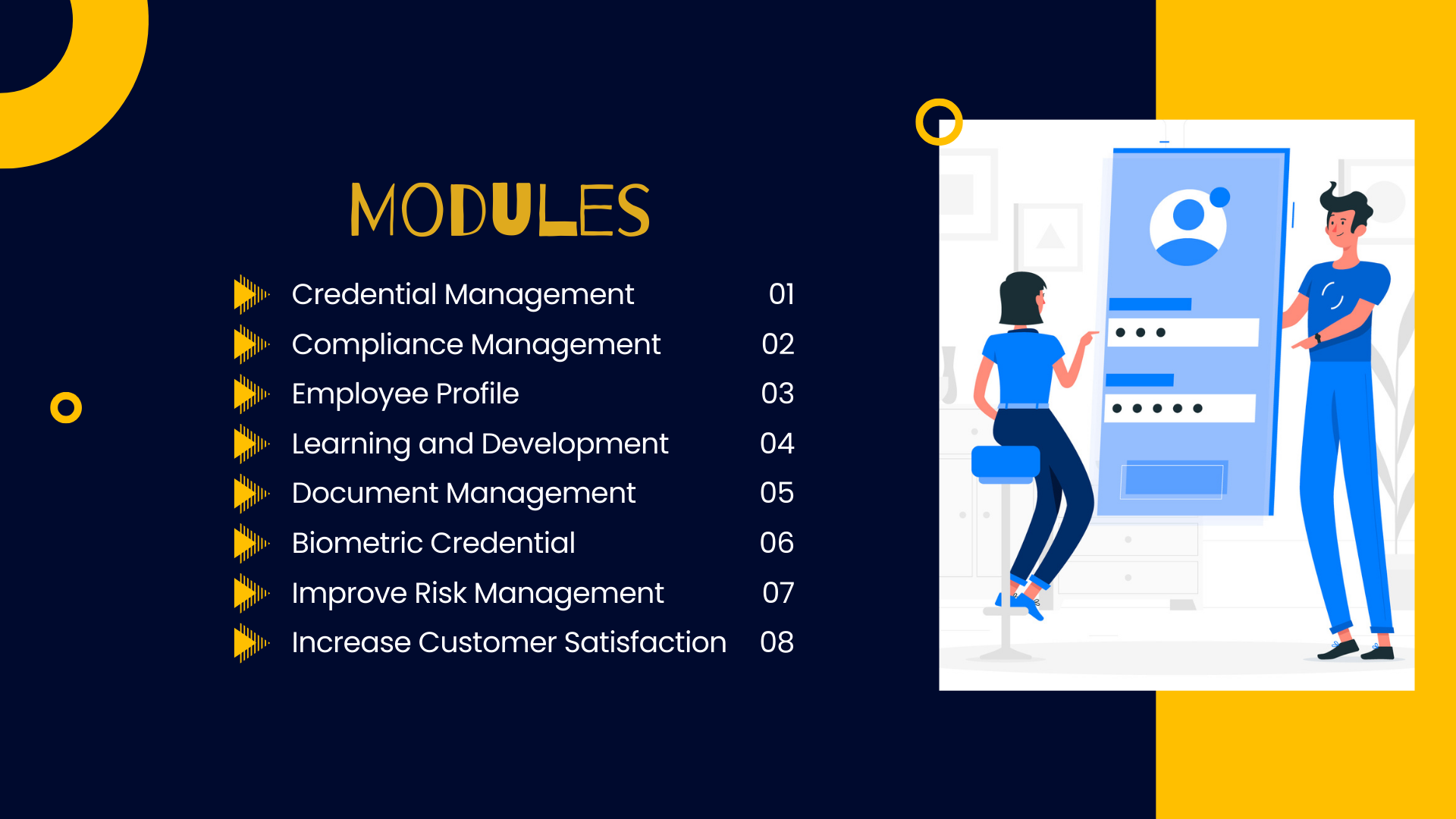
FutherMain Features
To try the most advanced business

Biometric credentials
These include fingerprints, facial recognition, and other biological patterns used to identify individuals. Biometric credentials are increasingly popular due to their security and convenience.
- Fingerprints.
- Facial recognition.
- Voice recognition.
- Iris recognition.
- Palm or finger vein patterns.

Automate rotation and reduce credential risks
Automated features simplify the process of organization-wide management while keeping your business compliant. This also helps with continuous auditing and session recording.
- periodically changing keys.
- other security credentials.

Organizational security complexity
Creating a secure organization is a complex and vital aspect for any business or organization, that requires a systematic approach. Organizations must take a step-by-step approach to build secure processes and systems with the help of appropriate people, process, and technological controls.
- Confidentiality.
- Integrity.
- Authenticity.
- Availability.

Zero Trust
Zero Trust Compatibility By leveraging just-in-time (JIT) access, ephemeral certificates, and additional authentication methods, Zero Trust takes a “never trust, always verify” approach.
- Identify users, devices, and digital assets that need network access.
- Identify sensitive data.
- Create Zero Trust policy.
- Design Zero Trust architecture.
- Implement Zero Trust Network Access (ZTNA).
- Monitor your network.

Automate the onboarding process
Automating the KYC onboarding is a fundamental practice in effective credential management. Automation streamlines the collection and verification of customer data and accelerates the process, enhancing conversion rates. It also ensures that regulatory requirements are met, maintaining compliance with financial regulations. Such a fluid and faster approach to onboarding boosts operational efficiency and customer satisfaction by reducing waiting times and friction during the account creation stage.
- Compliance.
- Clarification,.
- Culture.
- Connection

Strong authentication
Strong authentication. Leverages the application workloads native characteristics to strongly authenticate applications and eliminate “secret zero”.
- Password Based Login.
- Multi-Factor Authentication.
- Biometric Authentication.

Security policy enforcement
Security policy enforcement refers to the process of ensuring that an organization's security policies are implemented and enforced across all systems and applications.
- managing network
- application connectivity
- access

Never share credentials
Cybercriminals are looking for anyone with resources willing to take the bait and give them access. No business or account is too small to be a victim. To prevent phishing attacks, users should never share login credentials over text, phone, or email.
- You have no control over how someone else uses your password.
- You cannot control who else sees or accesses your password.
- You cannot control how your password is exposed to vulnerabilities.

Log all user activity
User activity log events describe all domain and security management tasks that a user completes. Use the user activity log events to determine when a user created, updated, or removed services, nodes, users, groups, or roles. The Service Manager writes user activity log events when the Service Manager needs to authorize a user to perform.
- Activities logged in Users and Partners.
- Activities logged in Users Groups.
- Activities logged in Invites.
- Activities logged in Email sign-ins.
- Activities logged in Partner Access Requests.

Encryption
Encryption at rest ensures that user credentials are protected even if the system is compromised, as the data is stored in an encrypted format that can only be decrypted with the proper keys. Basic encryption types
- Advanced Encryption Standard (AES)
- Triple DES.
- Blowfish.
- Rivest -Shamir-Adleman (RSA)
Our Great Team

Sankar
Founder
Mohamed
Marketing
Divya
Designer
Sekar
Development Lead
Deepthi
HR Management
Vinoth
Sales HeadBuild Team Success
Our team of experts is dedicated to delivering innovative IT solutions that drive business success. With years of experience in software development, project management, and technical expertise, our team members are passionate about leveraging technology to solve real-world problems.
Support System
Our leaders inspire and motivate
Our developers create and innovate
Our project managers guide and support
Our quality assurance specialists ensure perfection
Our support specialists care and serve
Over 30.000 Customers
and let's see what are they saying














Lorem ipsum dolor sit amet consectetuer adipiscing elit euismod tincidunt ut laoreet dolore magna aliquam dolor sit amet consectetuer elit
Mark Nilson
DirectorLorem ipsum dolor sit amet consectetuer adipiscing elit euismod tincidunt aliquam dolor sit amet consectetuer elit
Lisa Wong
ArtistLorem ipsum dolor sit amet consectetuer elit euismod tincidunt aliquam dolor sit amet elit
Nick Dalton
DeveloperFusce mattis vestibulum felis, vel semper mi interdum quis. Vestibulum ligula turpis, aliquam a molestie quis, gravida eu libero.
Alex Janmaat
Co-FounderVestibulum sodales imperdiet euismod.
Jeffrey Veen
DesignerPraesent sed sollicitudin mauris. Praesent eu metus laoreet, sodales orci nec, rutrum dui.
Inna Rose
GoogleSed ornare enim ligula, id imperdiet urna laoreet eu. Praesent eu metus laoreet, sodales orci nec, rutrum dui.
Jacob Nelson
SupportAdipiscing elit euismod tincidunt ut laoreet dolore magna aliquam dolor sit amet consectetuer elit
John Doe
MarketingNam euismod fringilla turpis vitae tincidunt, adipiscing elit euismod tincidunt aliquam dolor sit amet consectetuer elit
Michael Stawson
Graphic DesignerQuisque eget mi non enim efficitur fermentum id at purus.
Liam Nelsson
ActorInteger et ante dictum, hendrerit metus eget, ornare massa.
Madison Klarsson
DirectorVestibulum sodales imperdiet euismod.
Ava Veen
WriterUt sit amet nisl nec dui lobortis gravida ut et neque. Praesent eu metus laoreet, sodales orci nec, rutrum dui.
Sophia Williams
AppleNam non vulputate orci. Duis sed mi nec ligula tristique semper vitae pretium nisi. Pellentesque nec enim vel magna pulvinar vulputate.
Melissa Korn
ReporterProduct Portfolio
Our Work
Integration and Automation
Centralized Repository-Store and manage all credentials in a single, secure location. Automated Tracking-Track expiration dates, renewal requirements, and compliance status. Real-time Alerts-Receive notifications for upcoming expirations, renewals, or compliance issues. Verification-Validate credentials against original sources or third-party databases. Reporting-Generate reports on credential distribution, compliance, and expiration.
Read More



Our Plan
To try the most advanced business
- System Storage Auditing
- Customized Reports
- Unlimited Training
- Data Migration and Developer Support
- 24X7 Online Support
- Direct Customer Visit for Customer Support
- Regular and Weekly Back up
- System Storage Auditing
- Customized Reports
- Unlimited Training
- Data Migration and Developer Support
- 24X7 Online Support
- Direct Customer Visit for Customer Support
- Regular and Weekly Back up
- System Storage Auditing
- Customized Reports
- Unlimited Training
- Data Migration and Developer Support
- 24X7 Online Support
- Direct Customer Visit for Customer Support
- Regular and Weekly Back up
Book A Demo
Contact Form
Kindly describe your request in details, and provide us your phone number to contact you back.